CIEM
Gestione dei diritti dell'infrastruttura cloud
Wiz analizza i diritti cloud e genera automaticamente policy di privilegi minimi in tutto il cloud, per aiutare i team a visualizzare, rilevare, assegnare priorità e correggere i rischi di identità (IAM).
Assumi il controllo delle tue autorizzazioni cloud
Wiz analizza i diritti cloud e le autorizzazioni effettive per aiutare i team a comprendere i rischi e l'esposizione relativi all'identità. Wiz esegue la scansione e rileva i segreti esposti e i percorsi di movimento laterale che potrebbero compromettere le risorse sensibili e genera automaticamente suggerimenti di correzione e policy di privilegio minimo.
Autorizzazioni di dimensioni corrette
Monitora le identità umane e di servizio e utilizza i suggerimenti guidati generati automaticamente per ridimensionare correttamente l'accesso e i diritti nel tuo ambiente.
Analizza le autorizzazioni valide
Wiz crea una mappa degli accessi effettivi tra tutti i principali e tutte le risorse, tenendo conto dei controlli di mitigazione avanzati nativi del cloud, inclusi limiti, ACL e SCP.
Segreti esposti e movimento laterale
Rilevamento senza agenti e senza attriti di segreti o credenziali trapelati che gli aggressori potrebbero utilizzare nel tentativo di accedere a risorse sensibili o assumere il controllo di account.
Applica i privilegi minimi nei tuoi cloud
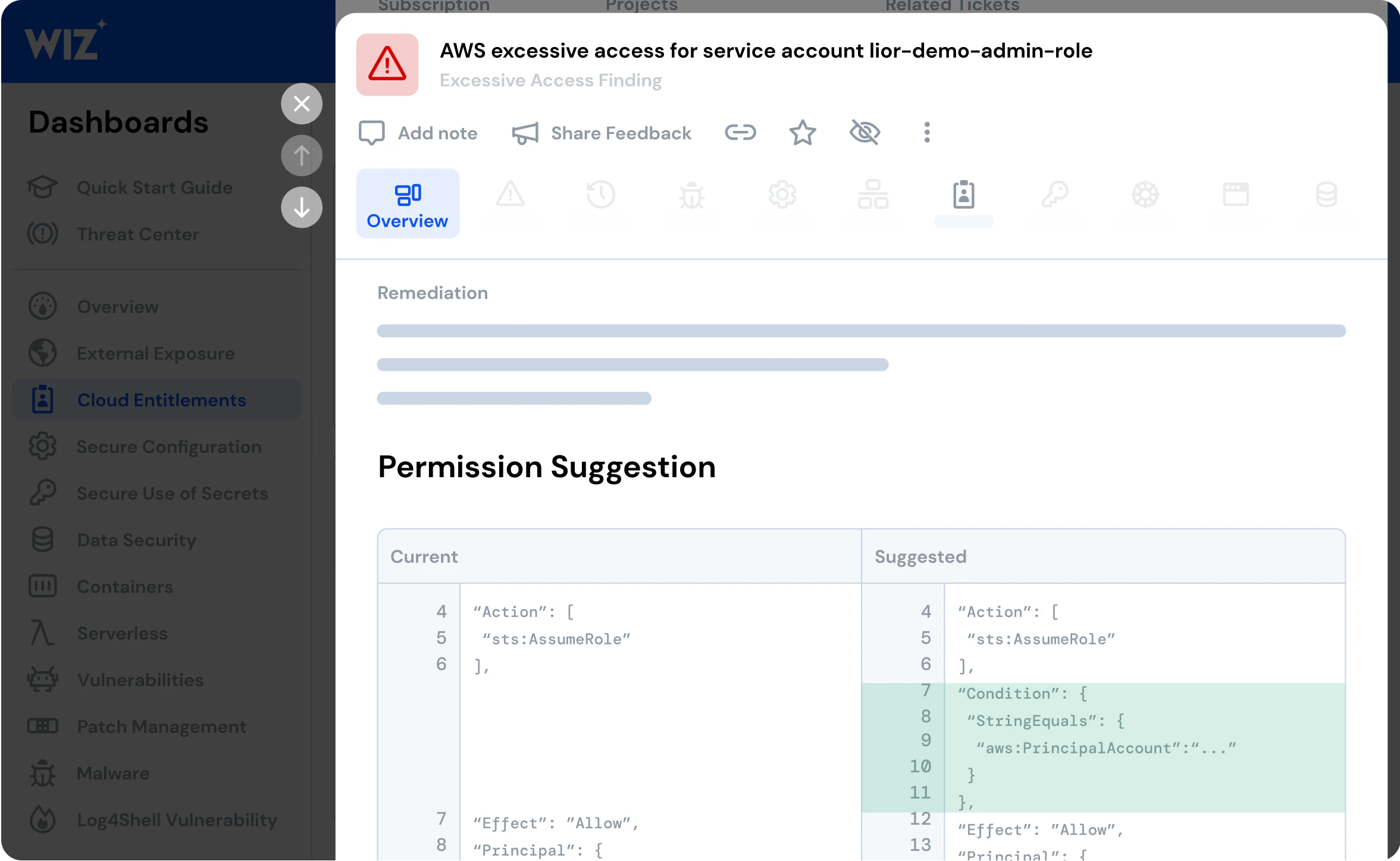
Andare oltre il CIEM
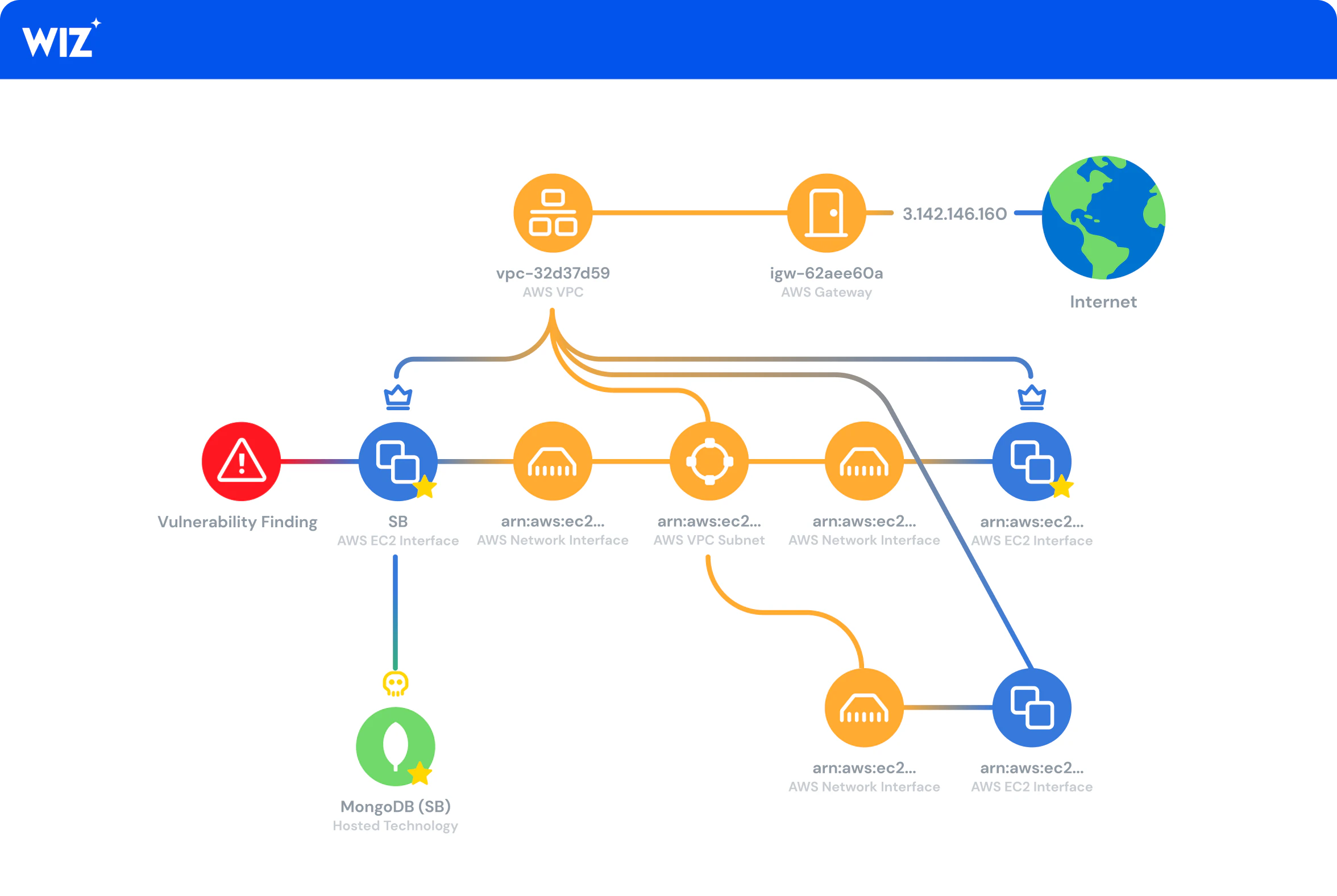
Connettiti in pochi minuti senza agenti
Sicurezza completa per AWS, Azure, GCP, OCI, Alibaba Cloud, VMware vSphere, Kubernetes e Red Hat Openshift. Incontra il tuo nuovo partner per la sicurezza del cloud.
Richiedi una demo personalizzata
Pronti a vedere Wiz in azione?
"La migliore esperienza utente che abbia mai visto offre piena visibilità ai carichi di lavoro cloud."
"Wiz fornisce un unico pannello di controllo per vedere cosa sta succedendo nei nostri ambienti cloud."
"Sappiamo che se Wiz identifica qualcosa come critico, in realtà lo è."

