Cloud-Transformation
Ihre Cloud umwandeln, sicher
Reife deinen Ansatz bei der Cloud-Sicherheit, um Risiken wirksam zu reduzieren und Innovationen zu entfesseln
Success criteria
Modernize Your Approach to Cloud Security
Transforming your cloud requires collaboration and coordination across teams and complex environments. Wiz enables you to unify and centralize your cloud security management, while rapidly removing critical risks across your cloud environments.
Understand Your Cloud
Build a comprehensive, shared understanding of your cloud environment. Reduce the risk of security breaches with a full view of your cloud technology footprint across your business.
Centralize Security Policies and Tooling
Consolidate your security tooling and improve your security stance, while implementing a unified approach to security policies that reduces security gaps across business units, environments and apps to drive operational efficiency.
Reduce Risk and Ensure Compliance
Accurately identify and remediate toxic combinations of your most critical risks across your business, including attack paths that lead to your crown jewel resources. Understand your compliance posture automatically organization wide or by segment of your business and focus your teams on what matters.
Democratize Security
Empower cross-functional teams with automated workflows and self-service access to remediation guidance to improve collaboration, drive developer efficiency, and eliminate cloud debt. Shift security left by preventing issues from reaching production.
Ensure Readiness
Continuously monitor for, identify and prioritize the next Log4Shell threat to reduce mean time to resolution.
Frictionless, Full Stack Visibility
Scan your entire cloud environment without agents with unified coverage across clouds and compute architectures with a one-time deployment that eliminates manual overhead. Visualize your environment with high-fidelity, actionable context to easily analyze evidence, understand risk and view cloud architecture, all without specialized training.

Enhance Security Through Effective Risk Reduction
Continuously correlate risk factors across multiple workload layers like vulnerabilities, exposed secrets, and malware with other risk factors like misconfigurations and network exposure to surface the toxic combinations that represent the most serious risks. Immediately identify workload exposure to the latest vulnerabilities sourced from Wiz Research along with numerous third-party threat intelligence feeds. Take remediation action with a single click or via automation rules.
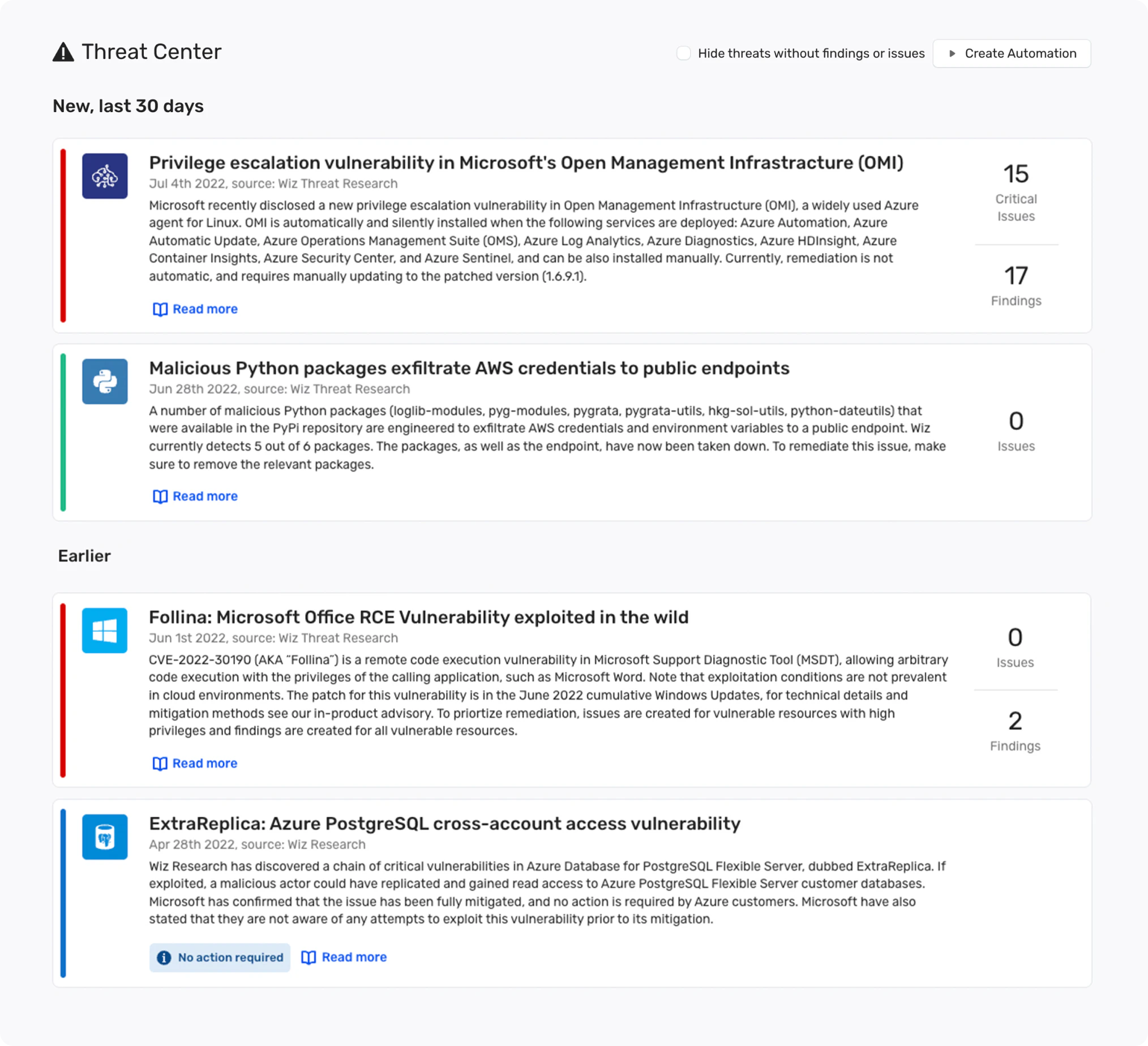
Empower Your Cloud Teams to Move Faster
Build partnerships with your engineering team to remediate and prevent security issues from reaching production. Segment Wiz so developers can self-service access just the parts of the infrastructure that they own with customizable workflows, a fully exposed API, and CI/CD tools to shift security left into the pipeline.
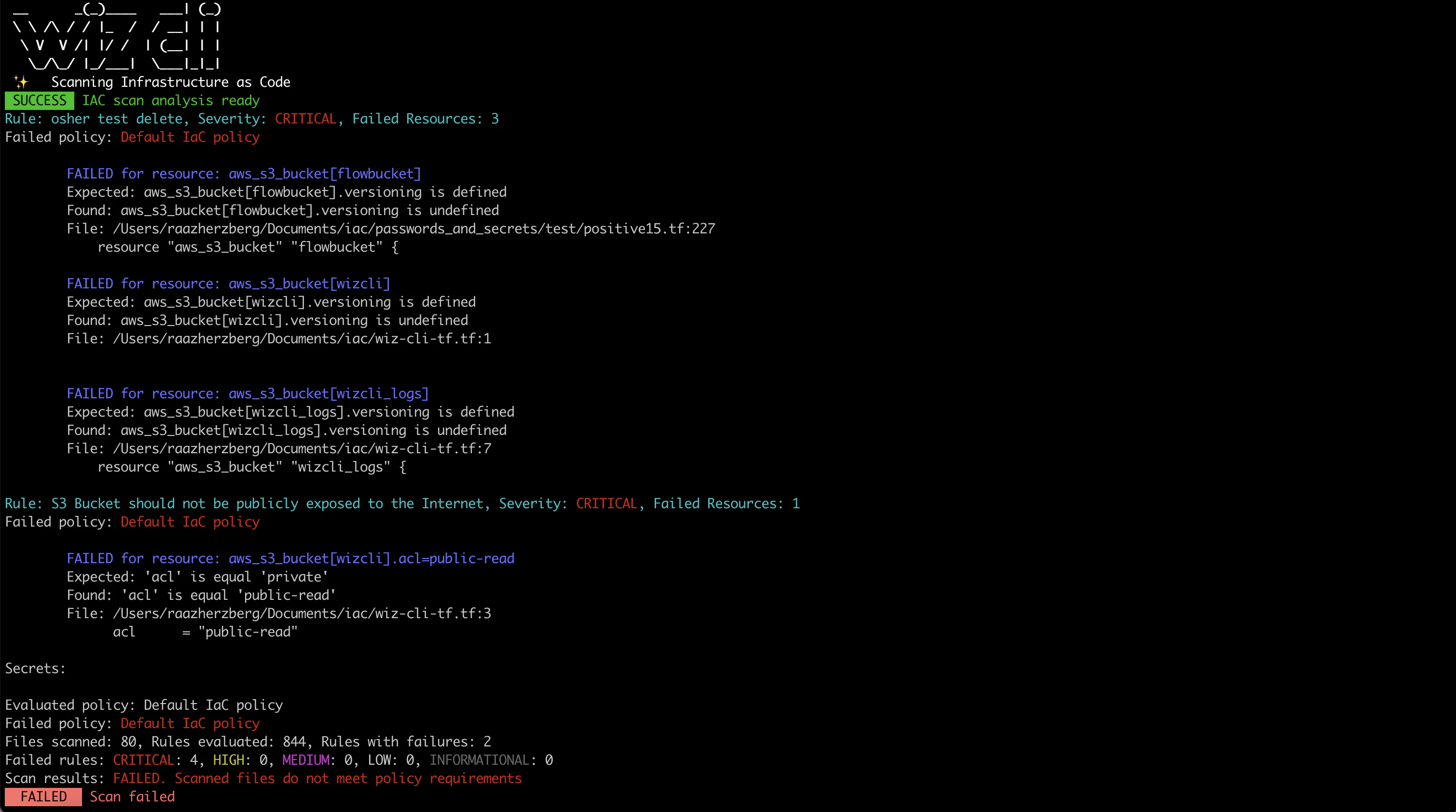
Automate Compliance
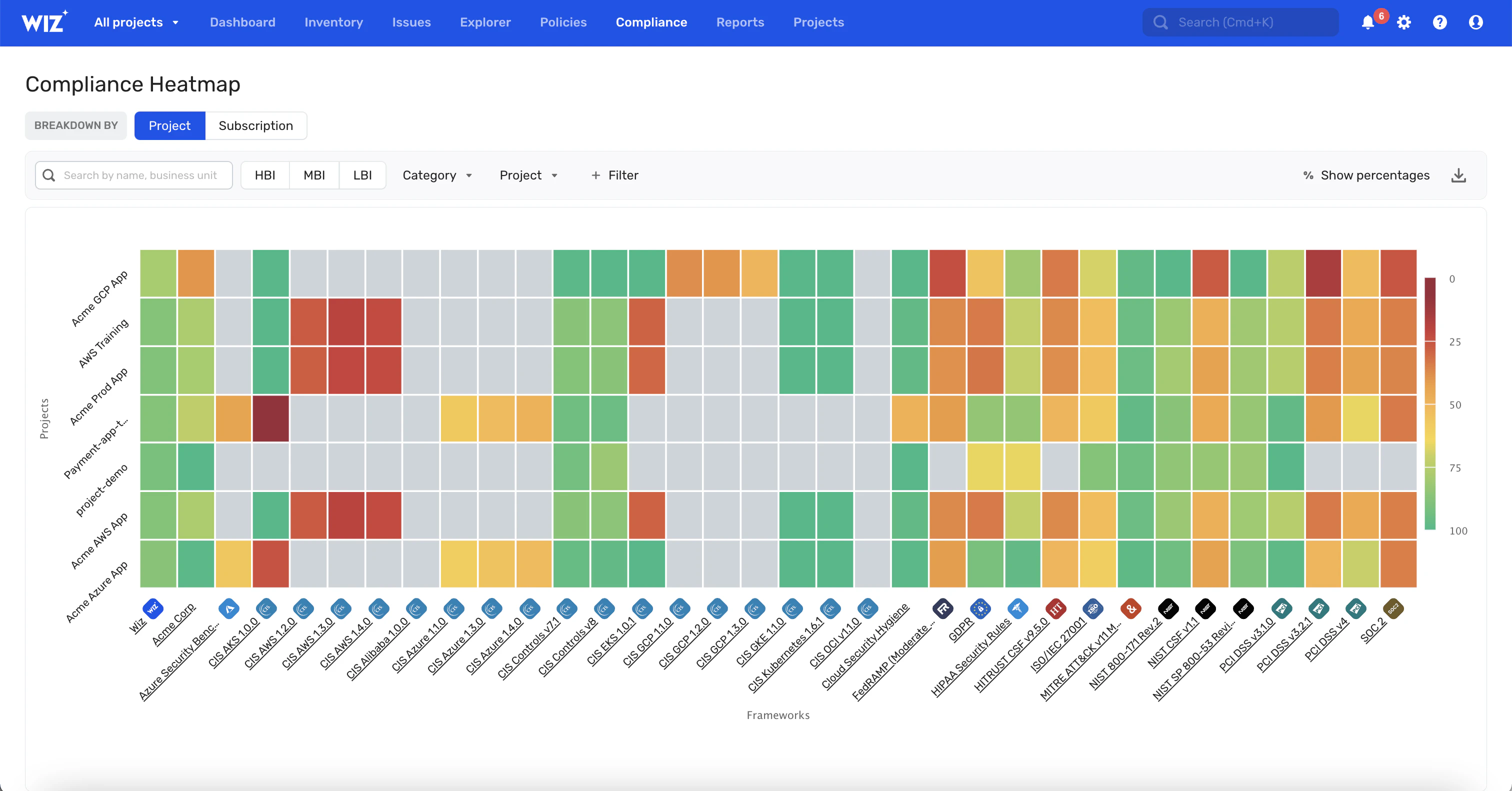
Use Wiz to maintain compliance with all major compliance frameworks and benchmarks. Get comprehensive assessments, posture scores, and a compliance heatmap. Quickly assess your compliance with high-level and granular detail, report it to your leadership with confidence, and focus your teams on what matters most.
Fallstudie
Blackstone setzt mit Wiz auf fortschrittliche Cloud-native Sicherheit
Als sich das Sicherheitsteam von Blackstone mit Cloud-Sicherheitslösungen beschäftigte, erkannten sie, dass sie ein Tool mit einem tiefen Verständnis der Cloud finden mussten, um das gewünschte Maß an risikoorientierter Sicherheit zu erreichen, das ihnen hilft, sich auf Schlüsselbereiche und nicht auf isolierte Probleme zu konzentrieren. Und dann fanden sie Wiz.
Fallstudie lesenEine personalisierte Demo anfordern
Sind Sie bereit, Wiz in Aktion zu sehen?
"Die beste Benutzererfahrung, die ich je gesehen habe, bietet vollständige Transparenz für Cloud-Workloads."
"„Wiz bietet eine zentrale Oberfläche, um zu sehen, was in unseren Cloud-Umgebungen vor sich geht.“ "
"„Wir wissen, dass, wenn Wiz etwas als kritisch identifiziert, es auch wirklich kritisch ist.“"

