Understanding credential access
Credential access is a cyberattack technique where threat actors access and hijack legitimate user credentials to gain entry into an enterprise's IT environments. The proliferation of cloud-based services and infrastructures has magnified the potency of credential access: According to IBM’s Cost of a Data Breach 2023 report, 15% of data breaches in 2023 resulted from compromised credentials. On average, businesses take almost 11 months to bounce back from credential-related data breaches, which is longer than any other kind of data breach. Credential access also results in the most financially damaging data breaches.
Let’s take a closer look at the consequences.
Expose cloud risks no other tool can
Learn how Wiz Cloud surfaces toxic combinations across misconfigurations, identities, vulnerabilities, and data—so you can take action fast.

Why is credential access so dangerous?
Credential access can lead to expensive and complex data breaches
Three out of twenty data breaches are the result of credential access attacks. As mentioned above, these data breaches are typically the hardest to remediate and the most damaging. With unauthorized access to systems, threat actors can launch cyberattacks such as advanced persistent threats—attacks that involve the stealth takeover of IT environments and data exfiltration.
It’s a critical step in an attack life cycle
In a cyberattack life cycle, credential access is a foundational step for threat actors. Because of the widespread adoption of cloud services, every organization has a trove of users, service accounts, groups, permissions, and roles that run their IT estate. Once a threat actor gains initial access to a system, hijacking any of these user credentials with other tactics like privilege escalation and exfiltration can significantly escalate attacks.
The Atlassian data breach, reported in 2023, highlights how credential access fits into an attack life cycle. To engineer this data breach, threat actors began by stealing employee credentials, but the attack didn’t stop there. Next, they used those valid account credentials to exfiltrate data from Envoy, one of Atlassian’s third-party providers.
Credential access is difficult to recognize
Unlike some other tactics, credential access provides cyberattackers with an invisibility cloak to evade detection. This silent tactic enables adversaries to orchestrate malicious activities, move laterally, access data, and manipulate permissions and security configurations without drawing attention to themselves.
Introducing the Cloud Threat Landscape, a new TI resource for cloud defenders
En savoir plusAttacks can bypass security tools
Most cybersecurity and cloud security tools focus on identifying and red-flagging malicious behaviors and unauthenticated users. Credential access allows adversaries to lurk in IT estates and cloud environments under the guise of legitimate accounts. Security mechanisms such as firewalls will almost always fail to red-flag hijacked accounts. From the perspective of security tools, there’s nothing suspicious about an active legitimate account in an enterprise’s IT estate.
Credentials are sold in illicit marketplaces
Cybercriminals often catalog and sell stolen credentials in illicit marketplaces, typically on the dark web. Other adversaries and hacker collectives may purchase these stolen credentials and use them to facilitate larger and more devastating attack campaigns.
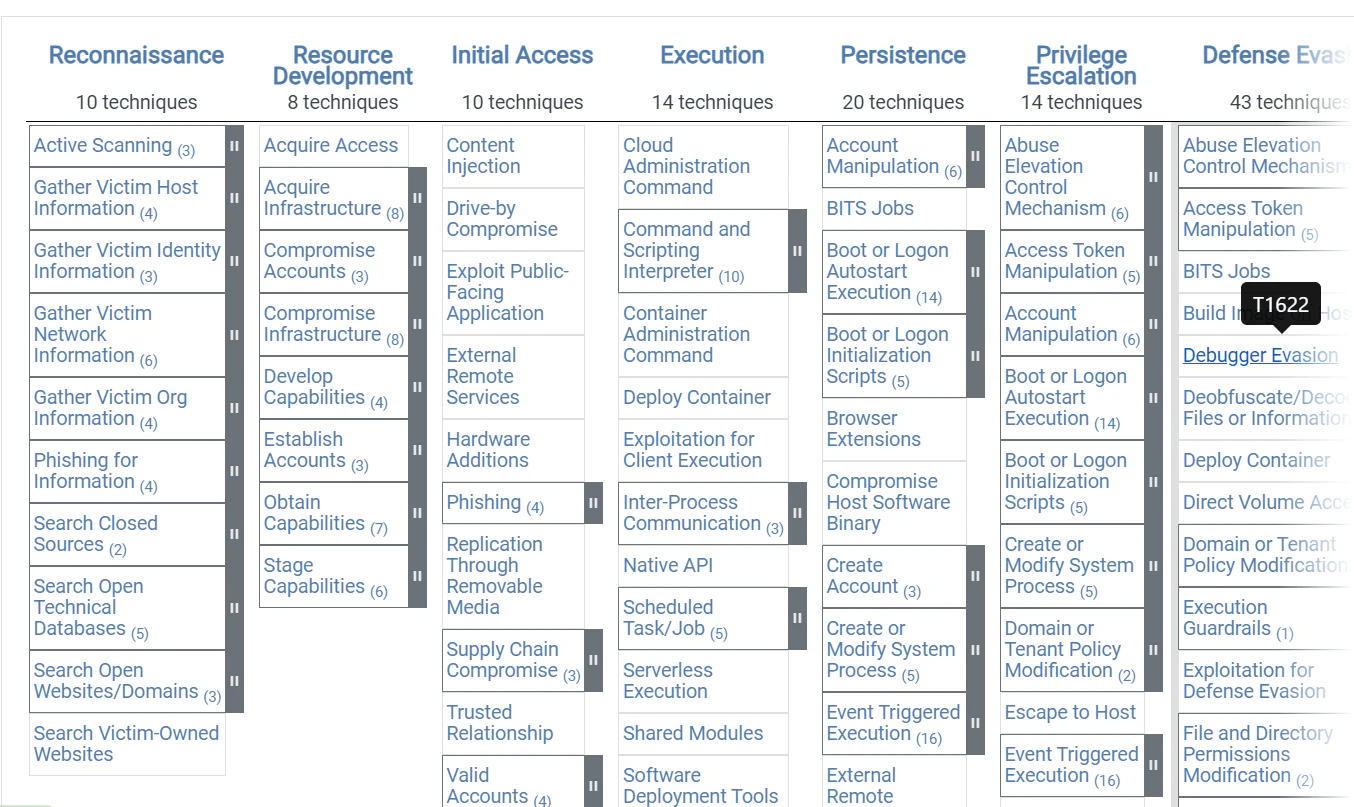
What are the MITRE ATT&CK techniques associated with credential access?
Credential access is one of the tactics emphasized in the MITRE ATT&CK Matrix for Enterprise, a cybersecurity framework and toolkit that can help businesses protect their operating systems and infrastructures. The MITRE ATT&CK framework is useful for many platforms, including Windows, PRE, MacOS, network, Linux, and containers. MITRE ATT&CK defines credential access as a tactic that involves threat actors stealing usernames and passwords.
In the MITRE ATT&CK framework, “tactics,” which also include execution and privilege escalation, describe an overall objective for cybercriminals. Each tactic has a set of related techniques (and subtechniques) that outline the steps threat actors take to meet that objective.
Here are the MITRE ATT&CK techniques associated with credential access:
Using adversary-in-the-middle: Adversaries situate themselves in the middle of two connected devices to gather sensitive information and escalate attacks.
Employing brute force: Threat actors who don’t possess known credentials attempt a trial-and-error method and try numerous passwords until they find the right one.
Obtaining credentials from password stores: Enterprises store their passwords in various repositories across their IT environments, which adversaries search to find credentials.
Exploiting for credential access: Threat actors exploit vulnerabilities and misconfigurations across cloud environments to access credentials.
Using forced authentication: By manipulating authentication systems and making legitimate users provide credentials via forced Server Message Block (SMB) and Web Distributed Authoring and Versioning (WebDAV) protocols, threat actors get keys to various segments in an enterprise’s IT environment.
Forging web credentials: Threat actors without credential access forge credentials to break into various internet services and applications.
Utilizing input capture: Using advanced tools, threat actors capture credentials when legitimate users type them in at various authentication checkpoints.
Modifying authentication progress: By manipulating authentication mechanisms and ecosystems, threat actors gain access to legitimate credentials. Unlike the "using forced authentication" technique, which involves SMB and WebDAV protocols, this technique modifies authentication processes like Local Security Authority Subsystem Service (LSASS), Security Account Manager (SAM), pluggable authentication modules (PAM), and macOS authorization plugins.
Using MFA interception: Adversaries steal legitimate credentials by interfering with increasingly popular multi-factor authentication (MFA) mechanisms.
Utilizing MFA request generation: By generating MFA requests for legitimate users, adversaries access and steal credentials.
Using network sniffing: With the network sniffing technique, adversaries hide and then surveil network traffic to find critical authentication data, including credentials.
Employing OS credential dumping: Threat actors scour OS caches to find credentials (either as password hashes or plaintext credentials). Dumping password hashes and plaintext credentials helps threat actors move laterally and escalate attacks. OS credential dumping subtechniques include Security Account Manager and cached domain credentials.
Stealing application access tokens: Threat actors steal application access tokens to gain access to remote services and data.
Stealing or forging authentication certificates: By stealing or forging enterprise authentication certificates, threat actors access remote resources.
Stealing or forging Kerberos/service tickets: Adversaries steal or forge Kerberos tickets (also known as service tickets), an authentication protocol that companies leverage across Windows platforms.
Stealing web session cookies: Cybercriminals steal web session cookies to gain access to internet services. By doing so, they can use internet applications and services without credentials.
Utilizing unsecured credentials: Cybercriminals search across files, registries, bash command history, private keys, APIs, group policy preferences (GPP), and chat histories to find and utilize unsecured credentials.
Best practices for mitigating credential access attacks
Follow these foundational best practices to avoid the dangers of credential access:
1. Strong authentication mechanisms
Multi-Factor Authentication (MFA): Require MFA for all accounts to add an extra layer of security.
Single Sign-On (SSO): Use SSO solutions to centralize authentication and simplify user management.
2. Least privilege principle
Role-Based Access Control (RBAC): Assign permissions based on the roles of users to limit access to only what is necessary.
Policy-Based Access Control (PBAC): Use policies to control access dynamically based on context and attributes.
Comprehensive Permissions Management: Use CIEM tools to gain visibility into and manage permissions across all cloud resources.
3. Regular credential rotation
Automated Rotation: Implement automated tools to rotate passwords, API keys, and other credentials regularly.
Short-Lived Credentials: Use short-lived credentials that expire after a brief period, reducing the risk if they are compromised.
4. Secure storage and transmission
Secrets Management: Use a dedicated secrets management tool to securely store and manage access to sensitive information.
Encryption: Ensure all credentials are encrypted at rest and in transit.
5. Monitoring and auditing
Continuous Monitoring: Monitor access logs and unusual access patterns using security information and event management (SIEM) systems.
Auditing: Regularly audit access controls and permissions to ensure they are still appropriate and detect any anomalies.
6. User training and awareness
Phishing Awareness: Train users to recognize phishing attempts and other social engineering attacks.
Security Best Practices: Educate users about security best practices, such as avoiding password reuse and using complex passwords.
7. Implement zero trust architecture
Micro-Segmentation: Divide the network into smaller segments to contain breaches.
Continuous Verification: Continuously verify user and device trustworthiness before granting access.
8. Leveraging a CDR tool for threat detection
Integrating a Cloud Detection and Response (CDR) tool into your strategy for mitigating credential access can offer advantages, such as:
Advanced Threat Detection: Use a CDR tool to detect and respond to potential credential access threats in real time.
Behavioral Analysis: Implement behavioral analysis to identify anomalies and suspicious activities that could indicate compromised credentials.
Automated Response: Configure the CDR tool to automatically respond to detected threats, such as disabling compromised accounts or revoking access tokens.
How Wiz can help
Wiz Cloud Detection and Response (CDR) can detect credential access tactics through its comprehensive detection capabilities, which include single event rules, correlation rules, and controls. These rules can generate Threat Detection Issues, providing various investigation and response capabilities.
To detect credential access tactics, Wiz CDR leverages:
Cloud Logs and Signals: Wiz ingests cloud logs and other signals, enriching them with additional context to identify suspicious activities.
Runtime Sensor: This unique sensor provides real-time monitoring and detection of malicious activities, including credential access attempts.
Security Graph: The Security Graph models your environment's security posture, helping to identify and correlate potential credential access events.
Threat Detection Rules: These rules can be customized to detect specific credential access tactics, such as unusual login attempts, use of compromised credentials, or access to sensitive data.
For example, you can query for specific IPs or events that triggered CDR rules related to credential access attempts. This helps in identifying and responding to potential threats effectively.
Get a demo now to see for yourself how Wiz keeps enterprises safe from credential access.
See Your Cloud Activities Come to Life
Schedule a demo to learn how Wiz can detect and analyze threats in context so that you can prioritize, investigate, and respond quickly to the right risks.