Container & Kubernetes security
Prevent attack paths at every step
Rapidly build containerized applications without risks. Holistically secure containers, Kubernetes, and cloud environments from build-time to real-time.
The Wiz Way
Cross-cloud contextualized container & Kubernetes security
Get complete visibility across containers, Kubernetes, and cloud environments in minutes without agents. Leverage the power of the Wiz Security Graph to analyze and prioritize risk with complete context. Detect real-time malicious behavior in Kubernetes clusters for rapid response. Enable a partnership between developers and security to shift left and resolve issues across the lifecycle of the containerized application.
Complete visibility
Scan all your containers, hosts, and clusters - across various Kubernetes setups, serverless containers, and standalone ones on virtual machines - to fully understand your containerized environments without blind spots.
In-depth risk assessment
Use the Security Graph to prioritize container risks by combining data from containers, hosts, cloud providers, and Kubernetes APIs. Identify vulnerabilities, misconfigurations, exposed internet-facing containers, excessive permissions, and leaked secrets. Take proactive measures to mitigate container risks and block potential attack paths into your environments.
Shift left
Collaborate with your development team to preempt container security issues across the SDLC. Secure container images from development to runtime. Scan the infrastructure’s code, including Kubernetes YAML files, Docker files, and Terraform, ensuring security compliance during deployment.
Secure containers across the lifecycle
Make your developers more productive at every stage by extending a single policy framework from production back to code.
Code
Scan IaC like Dockerfiles, Kubernetes YAMLs, Helm charts with Wiz Guardrails
Build & Store
Scan container images with Wiz Guardrails and registry scanning
Deploy
Block resources and container images security risks with Wiz Admission Controller
Run
Agentless scanning of running containers and sensor-based real-time threat detections
Graph-based risk correlation and prioritization

Automatic Kubernetes Security Posture Management (KSPM)
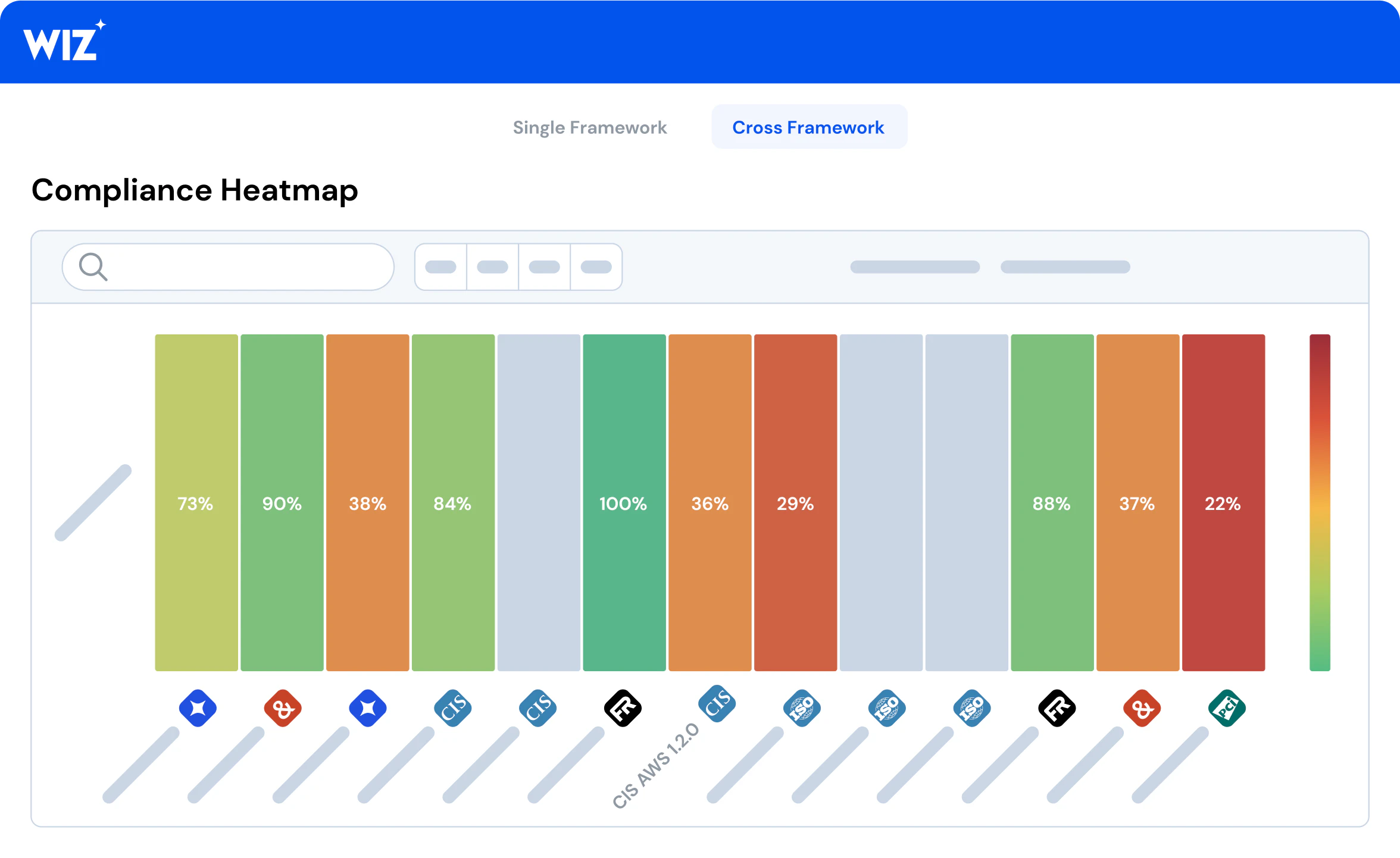
Real-time threat detection and response
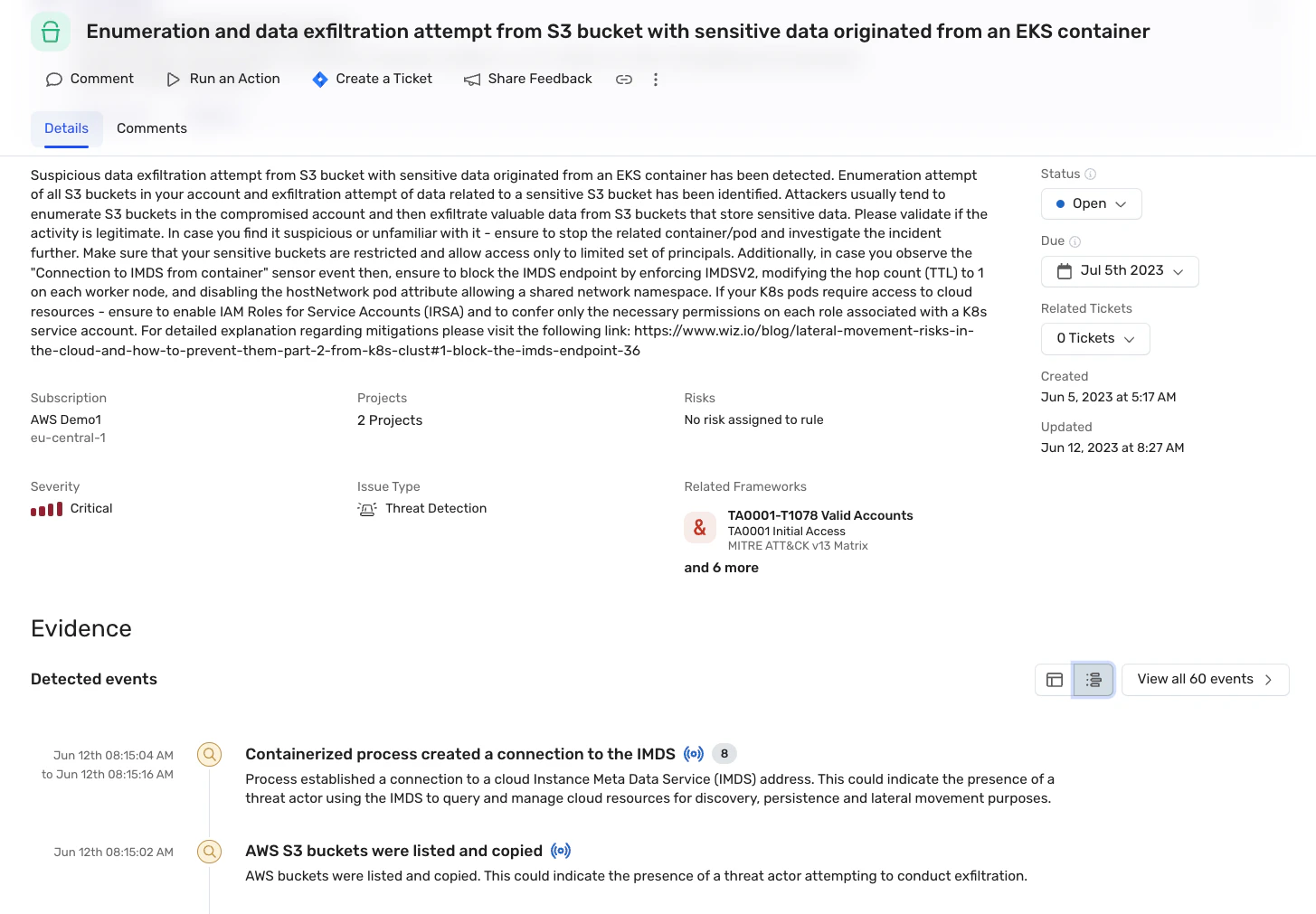
Enable guardrails across the development pipeline
Scan Infrastructure-as-code (IaC) files across Dockerfiles, Kubernetes YAML manifests and Helm charts for misconfigurations and security risks. Automatically assess one security policy across your entire cloud and Kubernetes development lifecycle and decide whether to block builds that violate it. Validate compliance with security policy before container images are deployed in the cluster.
Additional Resources
Get a personalized demo
Ready to see Wiz in action?
"Best User Experience I have ever seen, provides full visibility to cloud workloads."
"Wiz provides a single pane of glass to see what is going on in our cloud environments."
"We know that if Wiz identifies something as critical, it actually is."

